Step 4: Boot and Run the Keywriter#
This section demonstrates how to boot and run the keywriter using USB-DFU boot mode.
Documentation on booting using UART and OSPI modes can be found in the Keywriter Guide in MySecureSoftware.
Steps to boot and run keywriter#
Install USB-DFU
sudo apt-get install dfu-util
Configure the boot mode switches for USB-DFU boot mode.
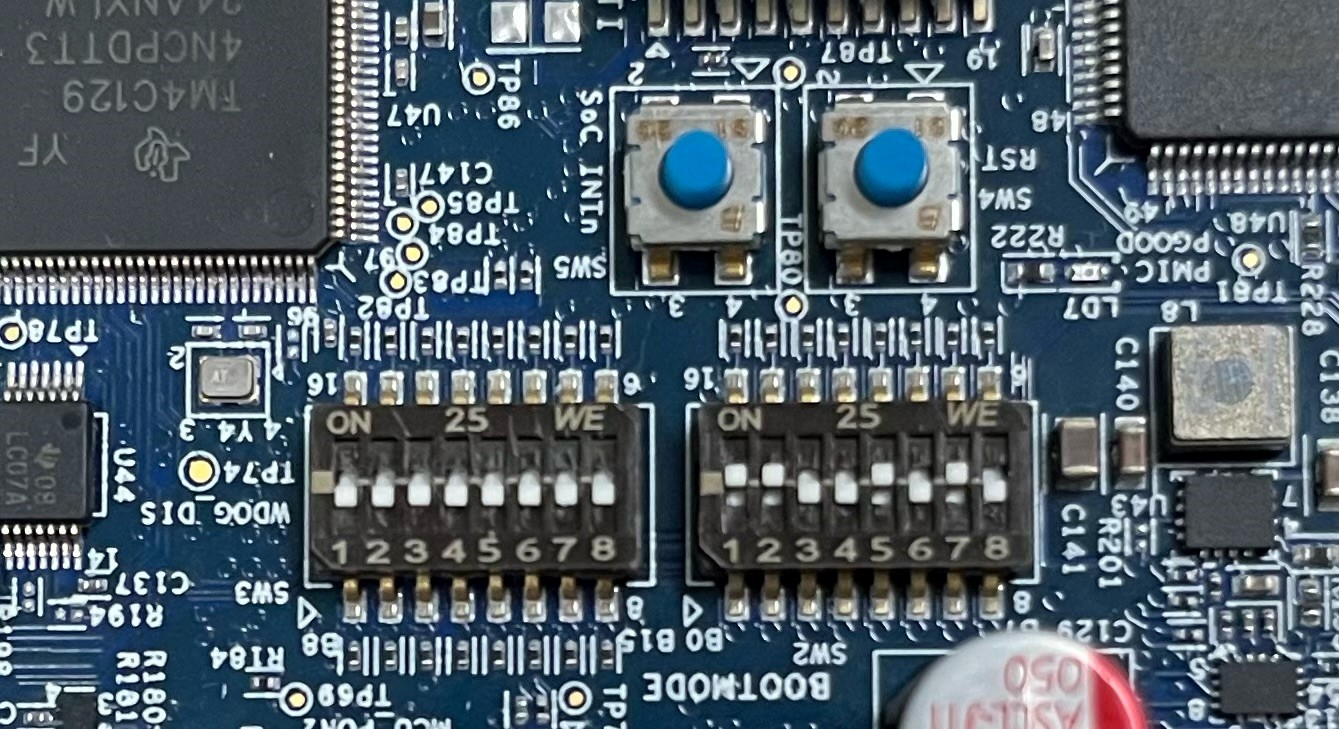
USB-DFU Bootmode#
Connect J17 (UART port) on the EVM to the Linux machine to be able to see the status logs. Open CCS, go to View -> Terminal. Click on “Open a Terminal”.
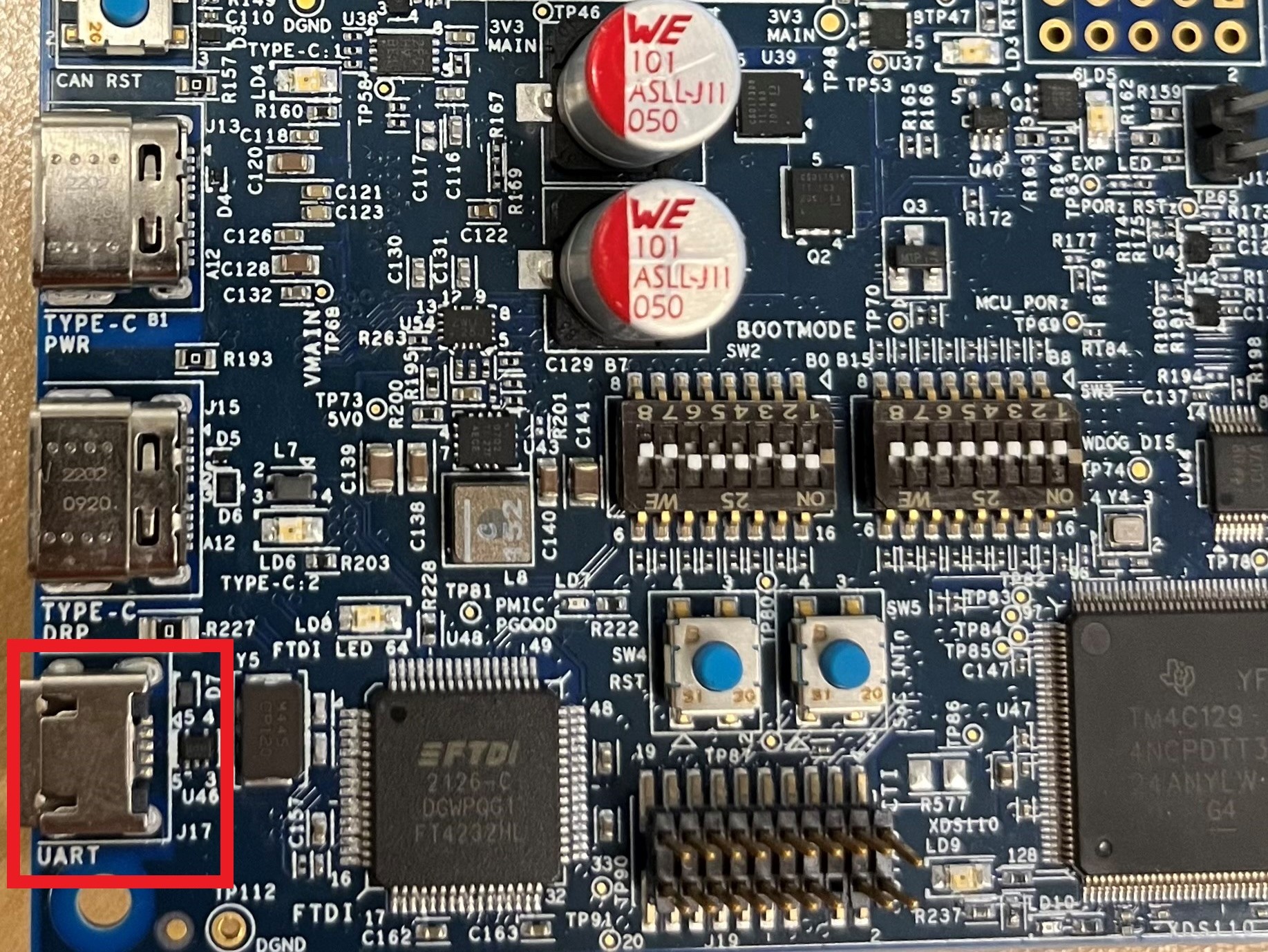
Port J17 on EVM#
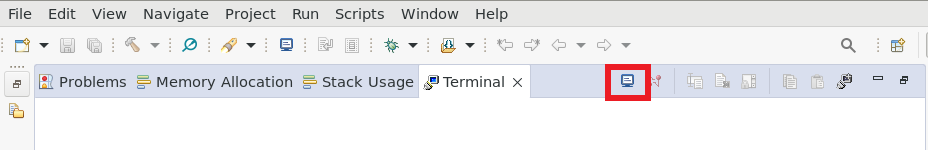
Open a Terminal in CCS#
Connect to the first USBxx port. Set the baud rate to 115200. Open another Terminal and connect to the second USBxx port. Ensure that the baud rate is 115200 for this connection as well. If no other UART devices are connected, these would be USB0 and USB1 respectively.
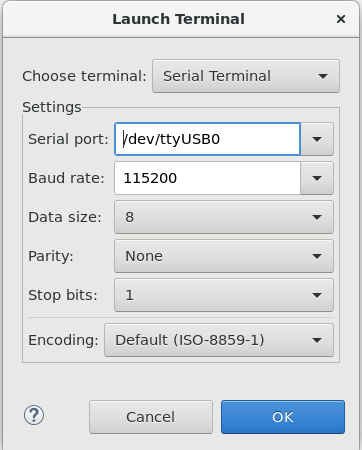
Terminal settings for USB0. Select the same settings for USB1#
Connect J15 (USB-DFU port) on the EVM to the Linux machine and J13 to a power source.
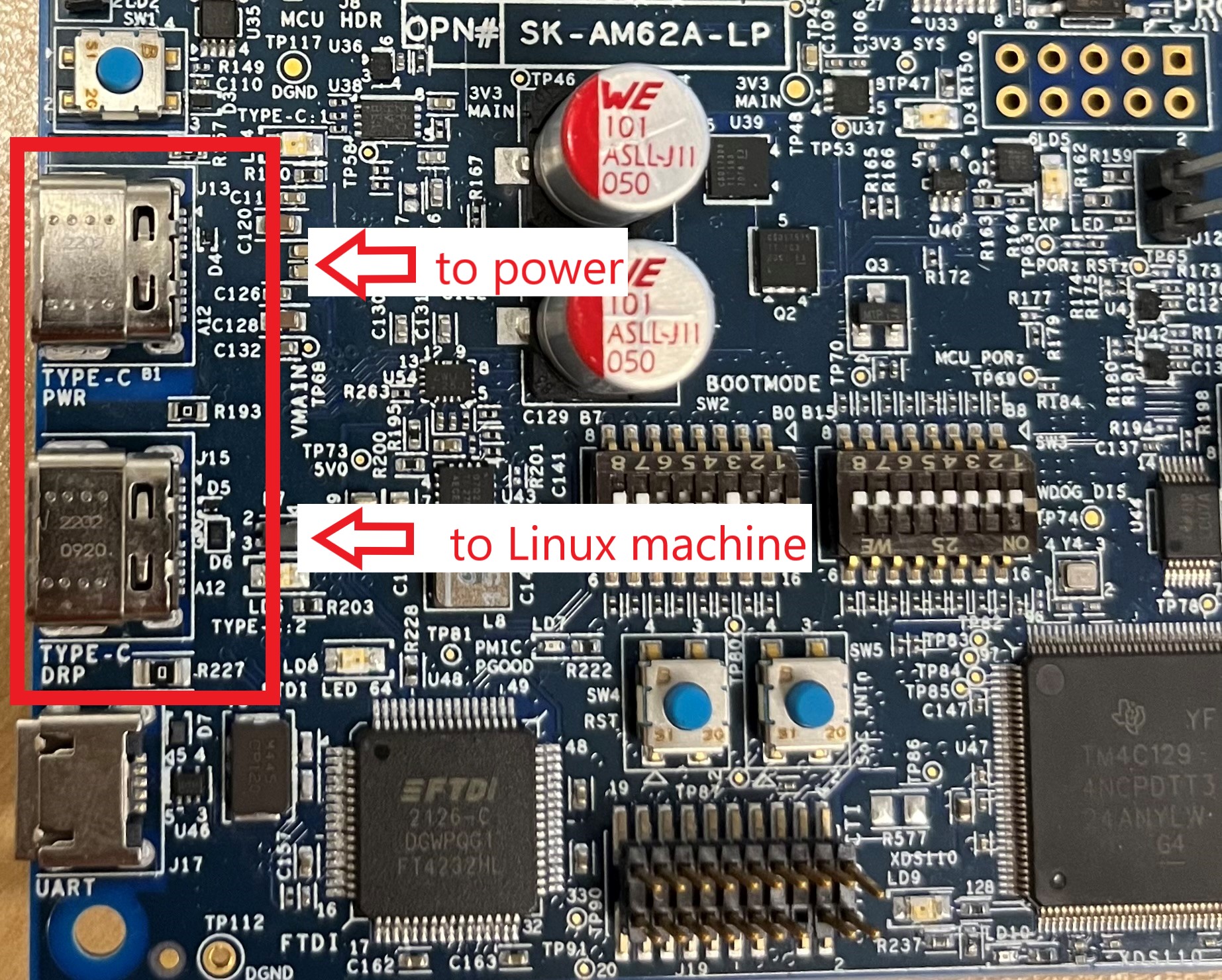
Ports J13 and J15 on EVM#
Verify that the device is being detected
sudo dfu-util -l
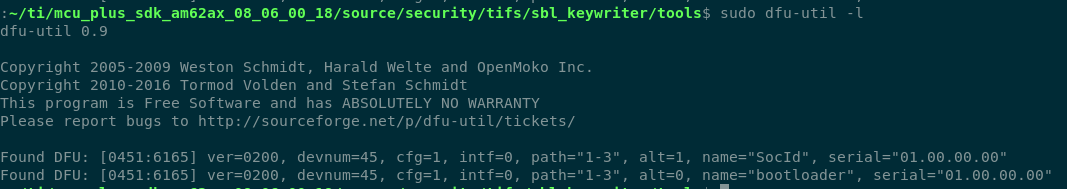
Check device detection#
Send the keywriter binary
sudo dfu-util -c 1 -i 0 -a bootloader -D <path_to_tiboot3.bin>
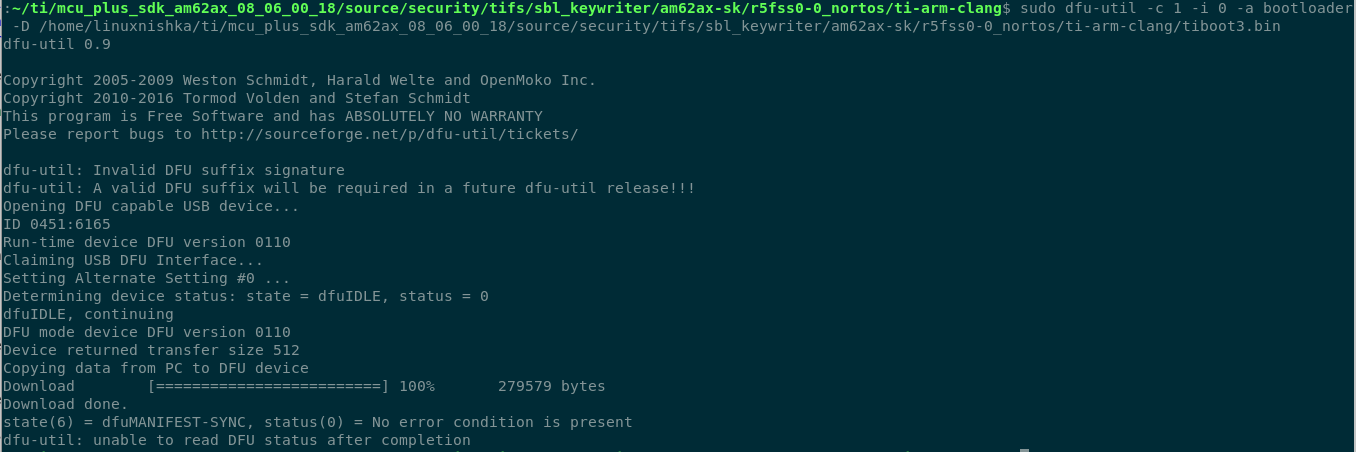
Check binary transfer success#
The R5 and M4 logs contain more detailed information about the key programming process. Here are example R5 and M4 logs on successfully booting and running the keywriter.
R5 logs#
[15:36:18.367] Starting Keywriting
[15:36:18.367] Enabled VPP
[15:36:18.367] keys Certificate found: 0x43c16800
[15:36:18.622] Keywriter Debug Response:0x0
[15:36:18.622] Success Programming Keys
M4 logs#
.WÍ08000
0x90000
0x400A78
0x0
0xFF922D4
0x8
0x409031
0x800023
#
# Decrypting extensions..
#
MPK Options: 0x0
MEK Options: 0x0
MPK Opt P1: 0x0
MPK Opt P2: 0x0
MEK Opt : 0x0
* SMPKH Part 1 BCH code: e050cadb
* SMPKH Part 2 BCH code: c099dd36
* SMPK Hash (part-1,2):
1f6002b07cd9b0b7c47d9ca8d1aae57b8e8784a12f636b2b760d7d98a18f189700
60dfd0f23e2b0cb10ec7edc7c6edac3d9bdfefe0eddc3fff7fe9ad875195527d00
* SMEK BCH code: a0c6de4e
* SMEK Hash: 92785809a3dfefea57f6bbed642d730ba5d05e601222a72e815bf01ceb3a50f96ab85d282425f684436fabd4c7da624b791da411615035314103cc64e611f532
* BMPKH Part 1 BCH code: c00807d5
* BMPKH Part 2 BCH code: 60311e36
* BMPK Hash (part-1,2):
07b5fd6f33cdba0c745bcc07e50805639713ec517614eac89754da1138d24dac00
5f1600a593b7100f0e1ca3c3a49e59b3622ab0651e08c0ffd2c88b04465cf7c900
* BMEK BCH code: a0da286f
* BMEK Hash: f5fbda1d62b46374de68e763ecd5a72227e7be73ca0d54a6d986ceb784b1bb0d06b6d95a8b399d421e41b7d3e7076220cd3992df255be068bd8924e86ae3a02d
EXT OTP extension disabled
* BCH code & MSV: fe0fac8b
* KEY CNT: 03030000
* KEY REV: 01010000
SWREV extension disabled
FW CFG REV extension disabled
* KEYWR VERSION: 0x20000
#
# Programming Keys..
#
* MSV:
[u32] bch + msv: 0x0
Programmed 2/2 rows successfully
[u32] bch + msv: 0x8BAC0FFE
* SWREV:
[u32] SWREV-SBL: 0x1
[u32] SWREV-SYSFW : 0x1
SWREV extension disabled
[u32] SWREV-SBL: 0x1
[u32] SWREV-SYSFW : 0x1
* FW CFG REV:
[u32] SWREV-FW-CFG-REV: 0x1
SWREV SEC BCFG extension disabled
[u32] SWREV-FW-CFG-REV: 0x1
* EXT OTP:
EXT OTP extension disabled
* BMPKH, BMEK:
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
* SMPKH, SMEK:
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
Programmed 11/11 rows successfully
Programmed 2/2 rows successfully
* KEYCNT:
[u32] keycnt: 0x0
Programmed 2/2 rows successfully
[u32] keycnt: 0x2
* KEYREV:
[u32] keyrev: 0x0
Programmed 2/2 rows successfully
[u32] keyrev: 0x1